This blog has been updated on – January 29, 2024
MuleSoft API security is a topic of discussion among data analytics service teams.
MuleSoft API security is a topic of discussion among data analytics service teams.
The rising cases of malicious cyberattacks on Application Programming Interfaces (APIs) also explain why companies are concerned about API security.
As per a recent study, the global API security market will grow at a CAGR of 26.3% from 2022 to 2032, valued at around $10,185 million. It indicates that securing APIs from uncertain data breaches is the foremost thing enterprises will prioritize.
Hence, MuleSoft services providers also need to learn the best practices to secure Mule APIs, servers, and databases from cyber attackers using Anypoint.
The goal is to restrict unauthorized access to the API information which is available for registered users, employees, and developers.
If you’re a MuleSoft developer or an enterprise needing a full-proof API security strategy, this blog is meant for you.
Table of Contents:
Why Is MuleSoft API Security Important for Enterprises?
The increased adoption of APIs for big data integration attracts some security threats.
API abuses are the most frequent cyberattack targeting enterprise web apps and systems. Such API security breach scenarios cost organizations over $600 billion yearly.
Knowing that APIs are susceptible to exposing sensitive financial, medical, and personal data, companies embracing MuleSoft API-led connectivity must take strict security measures to avoid risks.
We’ve got these pointers to understand the importance of API security in MuleSoft:
Customer Trust: Even a slighter risk of cyberattacks can tarnish your reputation and degrade your customers’ trust.
Besides that, the non-adherence to the MuleSoft API security standards can also result in financial losses, which will be more troubling for any business.
Security Standards & Regulations: API security standards are imposed on organizations dealing with customer data analytics and insights to prevent malware attacks.
HIPAA compliance is a cybersecurity initiative to control cyberattacks, typically in the healthcare and financial sectors.
Managed & Hosted Cloud Offering: MuleSoft developers deploy internal apps on CloudHub.
APIs integrated with this cloud hosting platform are exposed to external environments, raising serious security issues with access and authentication. Hence, focusing on MuleSoft API security becomes crucial when CloudHub or other cloud platforms are in use.
API security features on Anypoint can also tackle some significant MuleSoft data integration and enterprise challenges.
Want to strengthen your enterprise API security? Get secure and robust enterprise data management solutions from certified developers.
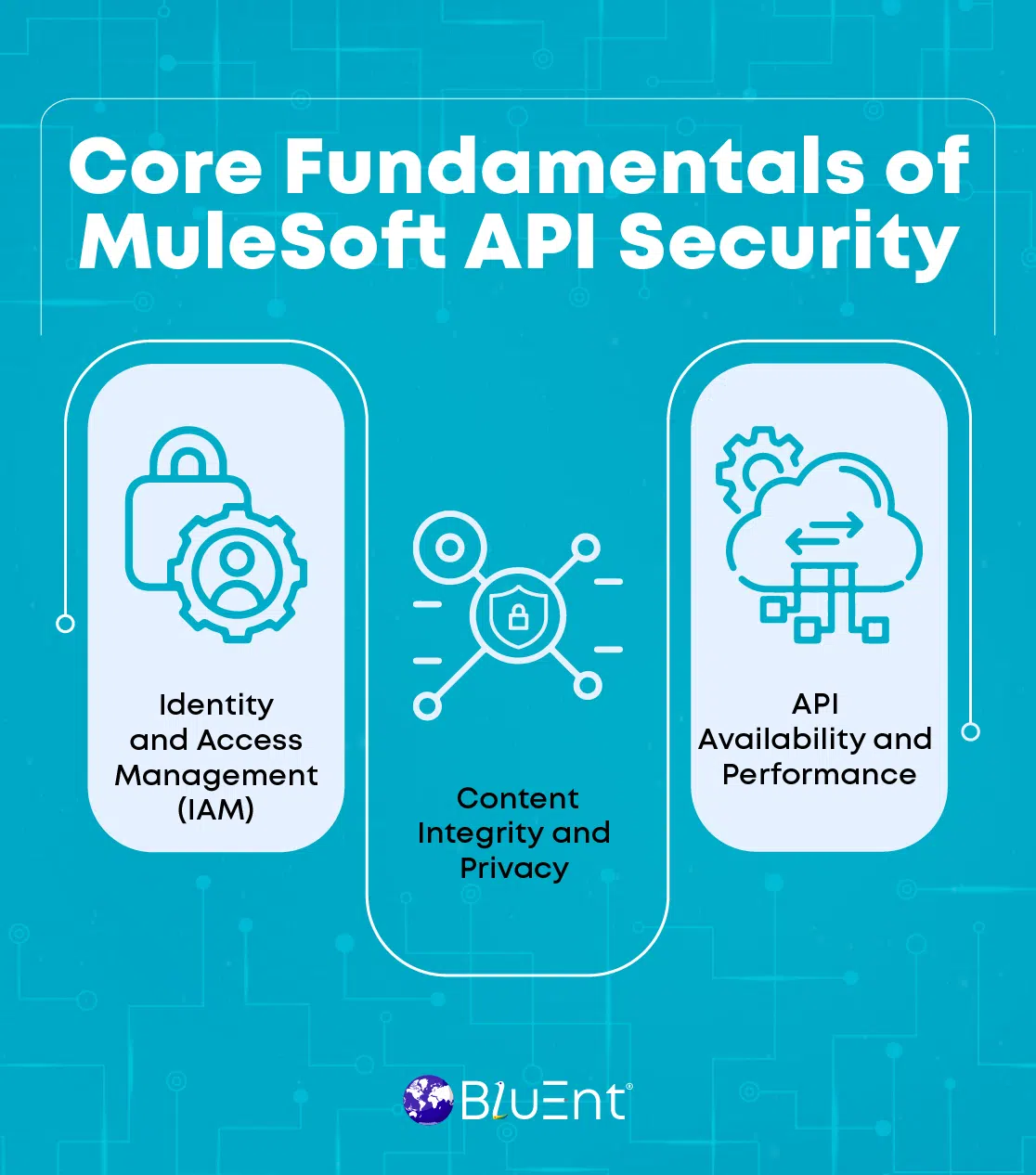
Key Principles of Enhanced API Security in MuleSoft Anypoint
Secure APIs are the key drivers of robust, managed, and integrated data infrastructure. They drive automation in business processes, enabling no-code development and efficient risk analysis and management.
MuleSoft API security ensures the confidentiality of the data shared among authorized users, servers, and apps. Additionally, any information or data insights gathered from clients and applications will remain secure from third parties.
If you want to secure your APIs using Anypoint, then check out the fundamental principles of doing so:
Identity and Access Management (IAM)
The first rule of API security in MuleSoft outlines roles and permissions to reuse APIs.
Besides data integration, MuleSoft Anypoint takes care of user authorization, identification, and authentication for access management. It helps developers govern the user roles and activities on API platforms.
Generating token-based credentials is another way to strengthen MuleSoft API security.
It issues a token when a user accesses APIs using username and password credentials for the first time. With this feature, users won’t have to share their account information over the network and that will not impose a security risk.
Content Integrity and Privacy
Another principle of API security in MuleSoft adds an extra layer of protection to incoming communications to apps.
The process is called content integrity, when a shared message remains uncompromised after being transmitted to the API. That focuses on that integral messages are not intercepted by external channels after transmission.
Content or message integrity ensures that shared messages remain protected and unaltered by suspicious parties. That may also be used for predictive analytics for risk management.
API Availability and Performance
Most internal enterprise apps running in the cloud are attached to diverse cloud and on-premises setups.
The database maintenance process, typically on cloud infrastructure, may attract a range of cyber risks.
The reason is the exchange or transmission of data from one internal app to another.
MuleSoft API security offers the ability to handle and respond to the transmitted messages without losing data and other risks.
Recommended Reading:
Delve into our big data case studies to see how we’re helping brands with data integration, management, and analytics needs.
5 Best Practices for API Security in MuleSoft
Let’s introduce some MuleSoft API security best practices that every data integration and migration team must learn.
Prioritize Identifying Business Logic Flaws
Business logic comprises a set of rules defining APIs’ limitations and how they operate. However, cyber attackers are more likely to target them for criminal activities.
In most cases, business logic flaws remain undetected even after going through strict performance tests as API builds and other features are error-free. Then how can cyber criminals take advantage of business logic flaws?
Attackers change the base functionality and use APIs that developers did not expect.
Testing every aspect of APIs and their features is the right approach to detecting business logic flaws. Try to access API using specific tools and compromise the data to analyze their performance.
Adopt a Zero-trust Security Approach with API Design
The zero-trust approach to improve MuleSoft API security in Anypoint is applied to API traffic.
Developers can’t neglect API traffic from both internal and external sources. However, they believe they won’t be exposed to cyber threats, noting that they’re not documented or available on public networks.
The best practice to deal with this API security issue is using a secure database design framework for identification and authorization purposes.
Focus on Multi-factor Authentication
Another way to secure your API on MuleSoft is multi-factor authentication that contributes to fraud data analytics and detection against API security risks.
It generates single-use token requests via apps once user credentials are already authorized.
Apply Shift-left Testing Methodology
Shift-left testing methodology asks for continuous testing in the software development process.
The goal is to run performance tests using the shift-run framework at each development stage and identify bugs or loopholes that can result in MuleSoft API security risks in the future.
Use MuleSoft API Manager for Added Security
API Manager adds to the security of APIs in MuleSoft. It comes up with an API proxy with every backend API implemented within Anypoint.
The API proxies are powered by an external API Gateway, ensuring a secure, faster, and easier implementation of API policies and concepts.
Control External Clouds and Third-party Services
As discussed earlier, APIs in cloud infrastructure such as MuleSoft CloudHub, Azure, and AWS are at higher security risks. The reason is the frequent exposure of MuleSoft endpoints to the external environment.
In such a scenario, data integration and management teams must limit the usage of external cloud and third-party services.
Recommended Reading:
Hire Certified Experts at BluEnt for API Security MuleSoft
The MuleSoft API security policies also emphasize tokenization, IP whitelisting, JSON and XML threat protection, client ID enforcement, and other risk prevention methods. However, every enterprise needs a MuleSoft-certified developer to make the most of them.
At BluEnt, we’re helping leading brands and enterprises with their data integration, management, migration, implementation, and migration needs. Our global presence of 7+ nations for over 20 years marks our credibility, quality, and prominence in business consulting, CAD and engineering, and IT services.
We’ve served numerous clients and delivered more than 11000 projects. Our service offerings include MuleSoft integration, data analytics, data science, CRM solutions, business process management, enterprise content management, etc.
Manage your APIs securely and smoothly with our team of certified MuleSoft professionals. Contact us today!
Frequently Asked Questions
How can Anypoint be used for API security in MuleSoft?
The following are the prominent features of Anypoint security for MuleSoft API:
-
Edge security: Add extra layers of defensive security with easy-to-configure and enterprise-grade edge gateways.
-
Auto hardening: Integrate Edge and API gateways seamlessly and identify API risks for protection.
-
Automatic tokenization: Prevent confidential API data breaches automatically with advanced tokenization services.
-
Sensitive information detection: Use prebuilt monitoring dashboards to track sensitive data and get alerts when found in API payloads.
What are the challenges of MuleSoft API security?
These are the two significant challenges of securing APIs in MuleSoft:
-
API standardization: Keeping up with five fundamentals of leveraging MuleSoft API security, including API governance, API protection, API data security, API discovery, and API security testing.
-
API sprawl: An issue that usually arises when too many APIs are slightly tricky to manage.













 The Power of Data in Enhancing Gift Card Customer Retention and Engagement
The Power of Data in Enhancing Gift Card Customer Retention and Engagement  Dell Boomi Integration Platform Explained: Architecture, Benefits, and Comparison with MuleSoft
Dell Boomi Integration Platform Explained: Architecture, Benefits, and Comparison with MuleSoft  Explainable AI (XAI): Bridge of Trust Between AI and Humans
Explainable AI (XAI): Bridge of Trust Between AI and Humans  How is the MuleSoft eCommerce Integration Platform Mitigating Retail Challenges?
How is the MuleSoft eCommerce Integration Platform Mitigating Retail Challenges? 
